GitHub, the web platform for teamwork on software development (sharing of source code for GPL or private rights, review and collaboration), has managed to keep its website accessible despite a DDOS attack that continues to fall on their servers since last Friday.
This seems to be Chinese hackers who have set their sights on the platform in order to show their dissatisfaction with the current development of projects.
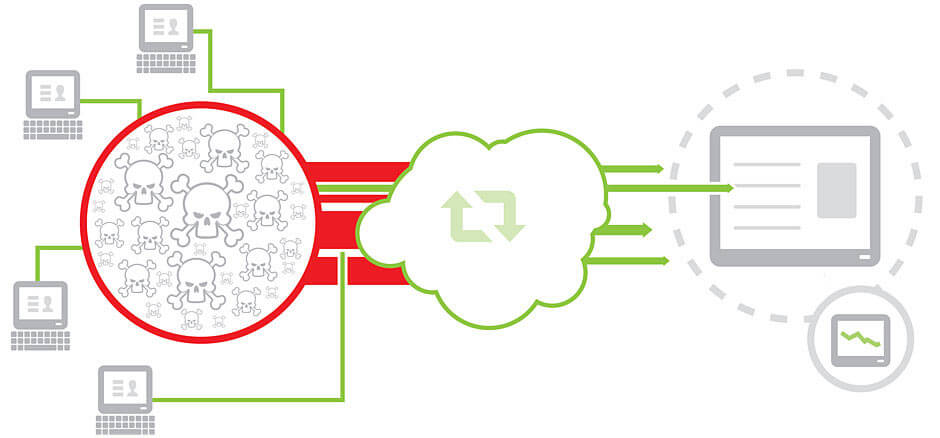
A DDOS attack is a denial of service attack, by sending thousands of requests to a server in order to render it inoperative in its ability to distribute the content. DDOS attacks are incredibly more complex and now requires a thorough approach to prepare for and manage the crisis when it happens.
How a DDOS attack take place?
A hacker or a group of hackers through several techniques take ownership of computers that have been infected by code (viruses). They divert the joint force of all these computers to a specific point and execute an attack. Like a crowd would take control of a traffic artery, heavy traffic slows the ability to run on it.
How to prevent DDOS attacks?
I do not think you can « avoid » a DDOS attack. This is something that may or may not happen to a business. These attacks are planned and designed a target for a reason more or less obvious. Let’s compare the DDOS attack as a terrorist attack, a way to be seen and heard of the mass by an unlawful act in order to harm, to cause damage and fear.
The tools available
Fortunately there is some tools available to better prepare for a DDOS attack. These tools must be combined with some talent of the network managers and be part of an effective action plain against hackers.
The goal is to « filter » the data to determine between good and bad requests and to separate them. The management of these « data packets » is then now possible. We need several layers of protection, to sucessfully filter the data packets.
The material
At the hardware level, there are routers such as CISCO, which are able to accurately identify the traffic in the network and assign them some rules. Management is facilitated for simple attacks by this equipment, but DDOS attacks are rarely simple as they were several years ago.
The use valid protocols makes detection more difficult to identify. As a first line of defense, these kind of routers do a good job anyway.
Firewalls play a vital role in the security of a company but not in the prevention of a DDOS attack. They will play their role by closing a specific access but are not able to handle and filter the data packets one by one.
The strategy
DDOS attacks are not easy to handle and some gaps in the layers of protection must be filled by another layer of protection. This is why a simple equipment will not effectively help you.
The Internet provider is expected to play its role and provide some protection and act as the first layer of protection. Next comes your router, firewall, the internal configuration of your server, the web application management (load balancer), memory management and cache, filtering protection on the root of the website etc.
Website Root Protection
Good management of the base of your website is often a step that you are able to do. Be sure to read our first article on the .htaccess file if your server operates under Apache. We defined in this article several important points for the safety of your website set up. There are others, and a specialist like our employees at the technical support, will help you with this.
If your site is under « WordPress », make sure it will not be hijacked by a gap in its code, by adding to your .htaccess file the following bit of extra code:
# XML RPC BLOCKING
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>
# /XML RPC BLOCKING
Otherwise, your web designer and web hosting company should provide you the layers of protection needed or the protection options to deal with such threats.